Hidden Dangers of Third-Party Logins: How to Safeguard Your Platform with Veri FIDO
March 14, 2025
Have you ever wondered how secure your platform is against phishing attacks?
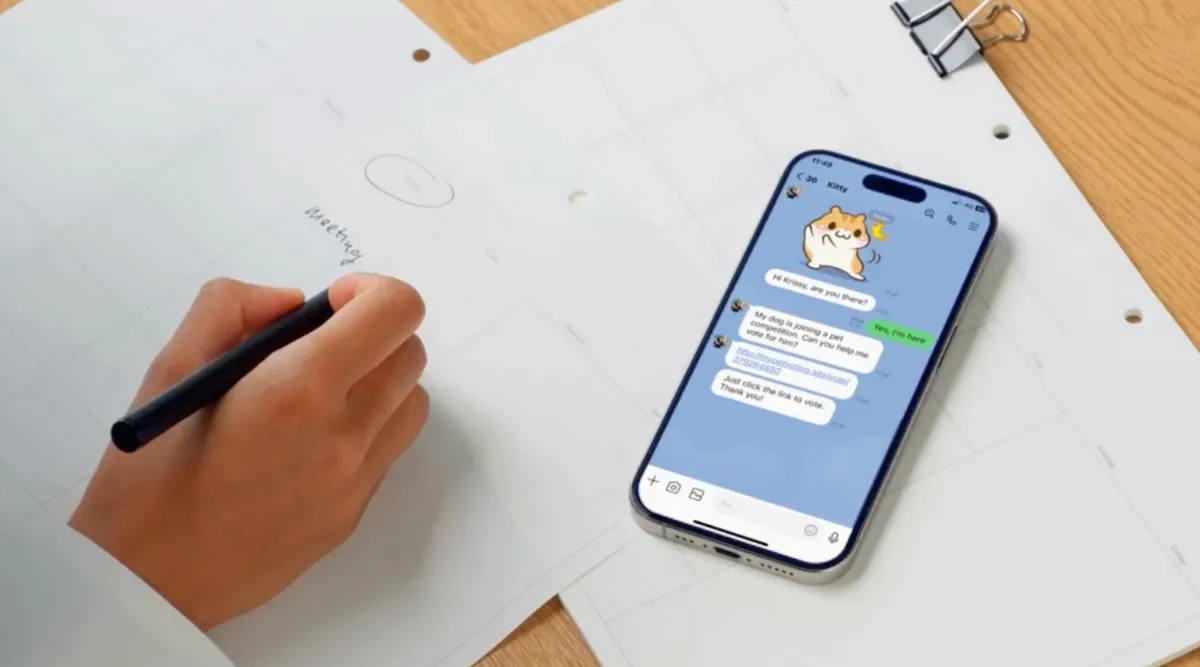
Imagine this: a user on your platform receives a message from a friend—"Can you vote for my pet?"—along with a harmless-looking link. They click, log in via Facebook or Google, and cast their vote, only to have their account hijacked within hours. The hacker then exploits the compromised social media credentials to seamlessly log into third-party platforms, amplifying the damage.
This isn't just a hypothetical scenario. Recently, multiple social media account takeovers have been reported, all traced back to phishing scams exploiting third-party logins. While logging in through platforms like Facebook, Google, or WhatsApp is convenient, it also opens the door to security risks that can leave both users and platforms vulnerable. In this blog, we'll uncover the hidden risks and provide actionable solutions to help you strengthen your platform’s security and protect your users from cyber threats.
The Security Risks of Third-Party Logins
Many websites offer convenient "one-click" login options through platforms like Facebook, Google, or WhatsApp, sparing users the hassle of remembering passwords. However, these third-party logins are directly connected to your social media accounts. If one of these accounts is compromised, the attacker gains access to all linked services, significantly increasing the potential for widespread security breaches.
Risk 1: A Compromised Social Media Account Puts the Third-party Login at Risk
When platforms rely on social media-based third-party login options, they effectively transfer account security control to an external provider. Hackers can gain instant access to all connected websites without requiring additional authentication if a user's Google, Facebook, or WhatsApp account is compromised.
For example, if a cybercriminal hijacks a user's Facebook account, they can access linked services. This could lead to unauthorized purchases, credit card fraud, and even identity theft, severely impacting both the user and the platform's reputation.
Risk 2: Single Access Point Becomes a Prime Target

Relying on third-party login options consolidates access to multiple websites under a few major social media platforms. This makes them prime targets for cybercriminals. If a vulnerability is discovered in a third-party provider, attackers can exploit it to gain control over numerous user accounts across various platforms. A single breach can have a domino effect, causing widespread damage.
The Reality of Social Media-Based Login Risks
WhatsApp is Among the Top 10 Most Imitated Brands in Phishing Attempts in 2025
WhatsApp accounted for 4% of global brand-related phishing attempts, highlighting the growing trend of cybercriminals exploiting popular platforms to deceive users.Google Warns of 'Clone Scams' Exploiting Login Portals
Google has issued warnings about 'clone scams' where cybercriminals mimic trusted websites or apps to deceive users. These scams often target login portals, taking advantage of user trust to steal personal information or sensitive data.
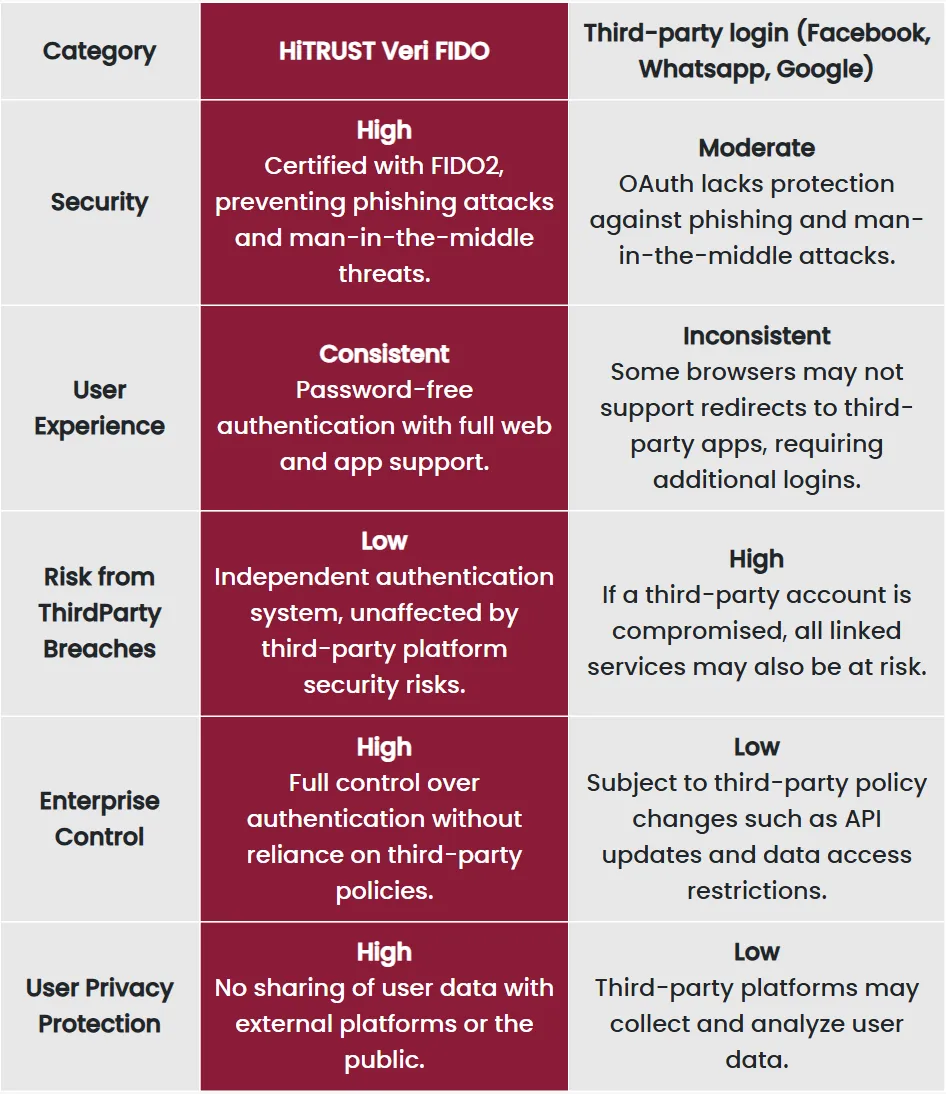
Veri FIDO — Secure, Seamless, and Password-Free Login
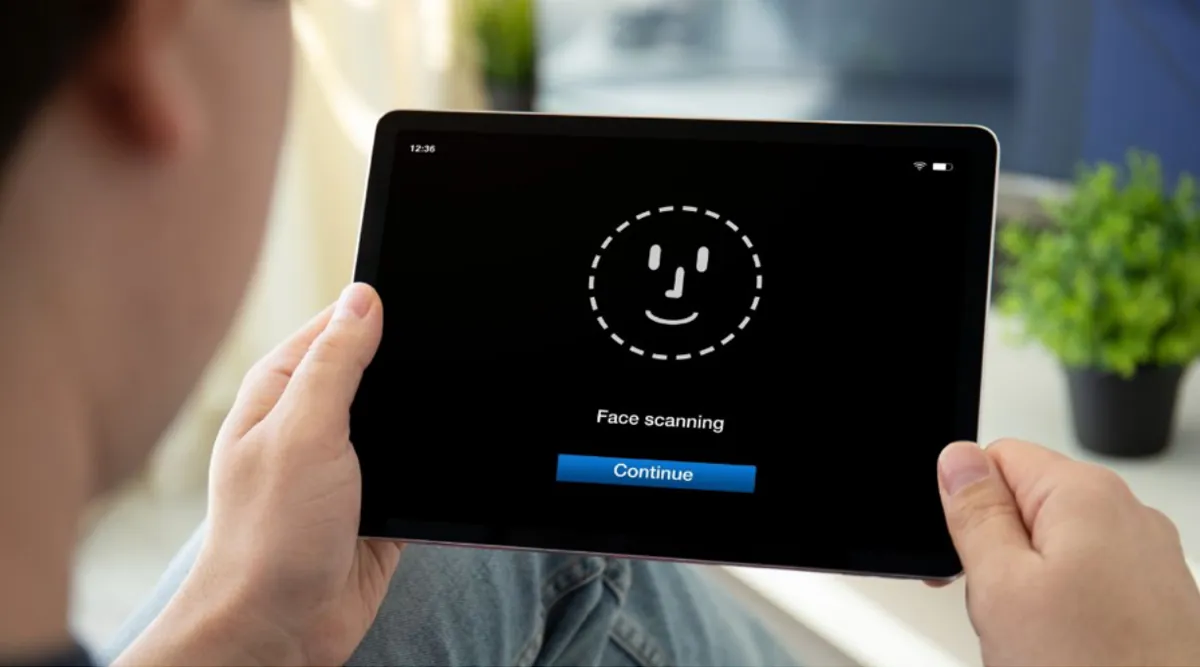
HiTRUST's Veri FIDO leverages the latest FIDO2-certified authentication technology, using public key cryptography and biometric verification (e.g. fingerprint and facial recognition) to provide a highly secure and convenient login experience.
By integrating Veri FIDO, platforms can eliminate password reliance, drastically reduce the risk of social media-based third-party login compromises, and give users utmost control over their accounts no matter where they're logging into. Using Veri FIDO, login security is no longer outsourced—it's fully in the hands of the users, achieving true passwordless and zero-risk authentication.
1. Enhancing user experience with passwordless login
Traditional authentication methods drive users to remember and manage many passwords, leading to weak security habits that are vulnerable to breach-led account takeover and phishing attacks. Veri FIDO replaces passwords with public-key cryptography, eliminating the “forgotten and reused” password dilemma. When adopting Veri FIDO for login at your platform, your users have the option to authenticate with biometrics (fingerprint, facial recognition, etc.) or hardware security keys instead of relying on passwords or social media credentials.
For example: A hacker sends a “vote for my pet” link to a phishing site. With traditional third-party logins, the user enters their Facebook or Google password, in which the hacker will steal. With Veri FIDO, there's no password input—authentication happens locally on the user's device, making phishing attacks ineffective.
2. Securing cross-platform authentication
Instead of relying on third-party providers like Facebook or Google for authentication, businesses can implement Veri FIDO for direct, decentralized login. This means:
-
No dependency on external social media platforms, reducing the risk of third-party data breaches.
-
User authentication remains under the business's control, improving regulatory compliance and security.
3. Protecting against Account takeovers
If a user's Facebook or Google account is hacked, attackers can access all linked services. Veri FIDO binds authentication to the user's device, ensuring that even if an attacker obtains a user’s social media credentials, log-in activities conducted without the physical device or biometric verification will not succeed.
Don't let third-party login vulnerabilities put your users at risk. Secure your platform today with HiTRUST's Veri FIDO and experience the future of authentication